Part I. The Basics
|
| What
is wardriving? |
| |
Wardriving is the gathering of statistics about wireless networks
in a given area by listening for their publicly available broadcast
beacons. Wireless access points (APs) announce their presence at
set intervals (usually every 100 milliseconds) by broadcasting a
packet containing their service set identifier (SSID; basically,
the user-defined name of the access point) and several other data
items. A stumbling utility running on a portable computer
of some sort (a laptop or PDA) listens for these broadcasts and
records the data that the AP makes publicly available.
When you wardrive, you drive around in your car while running a
stumbling utility, and record beacons from nearby APs. Most stumbling
utilities have the ability to add GPS location information to their
log files, so that the geographical positions of stumbled APs (often
called "stations" by insiders) may be retained and plotted
on electronic maps like those produced by Microsoft's MapPoint software.
The overwhelming favorite among stumbling utilities is called Network
Stumbler (informally, NetStumbler) and this FAQ will focus primarily
on the use of NetStumbler. Other stumbling utilities exist, and
I will provide pointers to them later on.
Wardriving as we know it was first developed by Pete
Shipley in April 2001. Others had run around with laptops, sensing
AP beacons and taking notes (often on paper!) but Pete was the first
to automate the process with dedicated software, and also the first
to integrate GPS location data with databases of detected APs. What
put wardriving on the map, however, was Marius Milner's NetStumbler
utility, which is by far the most widely used wardriving utility.
More—lots more—on NetStumbler later in this FAQ.
|
| Why
"war"? |
| |
This is kind of an unfortunate prefix, in these rather twitchy
times. Wardriving has nothing whatsoever to do with war. The term
is the offspring of the term wardialing, which was the (now
mostly extinct) practice of dialing random phone numbers via computer
to see if you could find an answer modem. Wardialing, in turn, came
out of the 1983 cult movie War Games, in which a teenager
got himself (and the rest of the world) into serious trouble by
creating an autodialer that eventually found its way into a DOD
computer programmed to wage nuclear war. The kid was looking for
computers supporting online games and had no strong intent to "break
into" anything—the problems that developed lay with an
essentially undefended military computer.
If I were the one coining a term, I'd coin something else, but
hey, the word is out there and we're using it.
|
| Why
is wardriving useful? |
| |
Wardriving provides a unique opportunity to gauge the growth of
a technology market segment by direct inspection. In other
words, we don't have to take a vendor's or research firm's word
for how many wireless networks are out there. We can go out and
look for ourselves. This isn't possible for things like digital
cameras and DVD burners. In conjunction with some understanding
of the demographics of an area, it's possible to use wardriving
data to get a sense for how "connected" or "tech
savvy" a neighborhood or region is.
This sounds dull, but in fact wardriving is fun in the sense that
a scavenger hunt is fun: You never know what you're going to find
when you go out, and you expect to be surprised. The wardriving
community is (as you'd expect) heavily connected via the Internet,
and you can meet a lot of interesting and extremely skilled network
and radio people by becoming part of the community. There is a lot
of sharing of technology knowledge within the community, in things
like network configuration and troubleshooting, antenna construction,
cabling and power infrastructure, and so on. Even though I've been
a licensed radio amateur (ham) since 1973, I tripled my knowledge
of microwave radio techniques by taking up wardriving.
|
| Do
you have to drive a vehicle to wardrive? |
| |
Not at all. In fact, in extremely dense urban cores like that of
New York, Washington DC, London, and Paris, it's much more effective
to simply walk around with a Wi-Fi equipped PDA in your pocket running
a stumbling utility like MiniStumbler on a PocketPC or Kismet on a
Zaurus. People have reported stumbling while riding bicycles and flying
airplanes. (In the air, it helps not to get too high.) What to call
these activities is unclear, so most of us just hang "war"
on the front of however we happen to be traveling. I go "warcabbing"
when I travel and don't rent a car, by opening my laptop in the back
seat of a taxi. |
| What
do I need to have in order to wardrive? |
| |
What most wardrivers call their "wardriving rigs" include
the following:
- A computer you can haul around with you. Most people use laptops.
Some use PDAs based on the PocketPC OS or Linux.
- A "stumbler" utility. By far the best known is Marius
Milner's Network Stumbler for Windows, which most people call
NetStumbler. Most major operating systems have stumbler programs
available. Linux has Kismet; MAC OS has MacStumbler. Marius has
ported NetStumbler to PocketPC, for which it's called MiniStumbler.
- A Wi-Fi client adapter supported by your chosen stumbler utility.
By far the best and most widely supported client adapter is the
Orinoco line of PC card adapters, now manufactured by Proxim.
The Orinoco line is inexpensive, very sensitive, and unlike 90%
of PC card Wi-Fi adapters, has a small jack for attaching an external
antenna.
- An external antenna attached to your client adapter. Ideally,
this is an omnidirectional vertical mounted on the vehicle roof.
These are small and resemble cell phone antennas. You can wardrive
with nothing more than a PC card's built-in antenna, but these
antennas are wretched and (being inside the vehicle) will be shielded
from signals to some extent by the vehicle's metal structure.
Note well: I do not think that Pringle's potato chip cans
make good wardriving antennas, but they're, well, legendary.
- A GPS receiver that emits NMEA 183 formatted data. This allows
the stumbler program to record where stumbled stations are located
in the physical world. Technically, GPS is optional, but the stumbled
data is much less useful without GPS information.
I'll cover most of these points in more detail later on in this
FAQ; specifically, Part III.
|
| Where
can I find more information? |
| |
Some suggestions:
- Keep reading this FAQ! (Lots more below!)
- Two chapters in my book, Jeff
Duntemann's Wi-Fi Guide,
Second Edition, are devoted to wardriving and interpreting
the data you gather while wardriving. The book is published by
Paraglyph Press. Its ISBN is 1-932111-88-3. 520 pages, $34.99.
- Read the threads on the NetStumbler
forums. Note that I said read. Although the forums
are well-used for asking questions, asking simple, obvious, asked-every-ten-minutes
kinds of questions will not make you friends on the forums. Don't
be a doof. Read—and learn to use the Search function—before
posting questions.
- Monitor Marius Milner's Stumbler.net
blog. Marius is the author of NetStumbler, the most widely-used
stumbling utility. His blog contains notes on release levels for
the program, new support for Wi-Fi client cards, and other things.
Beyond that, well, just Google around on the Web. The term "wardriving"
has only one meaning, so you won't get a lot of false hits. Many
individuals have posted enthusiast sites on wardriving, and you
can learn something from almost all of them.
|
Part II: Legalities
and Ethics
|
| Is
wardriving legal? |
| |
The legality of wardriving hasn't been tested, but few people think
that wardriving itself is illegal. What is certainly illegal
is connecting to and using networks without the network owner's
permission (which is what most people call "breaking into a
network") and wardriving has taken some hits in the press because
network crackers will sometimes use wardriving tools to locate networks
to break into. It's the ancient conundrum of the uses to which tools
are put: A crowbar is handy for taking apart pallets for use as
firewood, but a crowbar can also be used to break into buildings.
Should crowbars then be illegal? Hardly. The gotcha is that this
is a very new phenomenon, and the law hasn't entirely caught
up with networking as a whole, much less the peripheral issues that
emerge with regularity from the seething cauldron of technology
innovation.
To keep wardriving legal, it's important to 1) obey the law as
it exists today, and 2) do our best to encourage journalists to
draw the distinction between wardriving tools and their abuse by
crackers. Public perception is extremely important. If you connect
to other people's networks illegally, it's your butt in a sling
and nobody else's, but if you brag about it and the press picks
it up, you hurt us all.
|
| How
do I stay on the right side of the law while wardriving? |
| |
My fellow wardrivers and I adhere to a relatively strict code of
ethics that can be cooked down to the following:
- Don't look.
- Don't touch.
- Don't play through.
In other words, 1) don't examine the contents of a network; 2)
don't add, delete, or change anything on the network, and 3) don't
even use the network's Internet connection for Web surfing, email,
chat, FTP, or anything else. Somebody else paid for the bandwidth,
and if you don't have permission to use it, you're stealing it.
Basically, unless you have permission, don't connect. Consider
it a matter of personal honor, even when it's unlikely that you'll
be caught. (If you get too used to feeling that you won't get caught,
sooner or later you will get caught!)
|
| What
is autoconnection and how do I avoid it? |
| |
You don't always have to do anything deliberately to connect (illegally)
to someone else's network. Some client adapters are more "promiscuous"
than others and will hook up with any unprotected AP that comes
into range, given enough time to perform a DHCP transaction. This
is called autoconnection, and it's a problem for wardrivers
for two reasons:
- It's illegal to connect to a non-public AP without permission.
Period.
- Some client adapters will autoconnect to an AP, and then place
the SSID of that AP in the SSID field of the client adapter's
operating profile. After this, your stumbler program will not
log any additional stations with SSIDs other than that one. Your
wardrive is then basically over, even if you drive another fifty
miles.
Avoiding autoconnection is essential. Sometimes it can be prevented
by unloading your client adapter's client utility before setting
out on a wardrive. That may not, however, be enough. The only foolproof
way I know to prevent autoconnection is to disable all networking
protocols (TCP/IP, NetBEUI, NetWare, or anything else) on your
wardriving computer before setting out. Without a networking protocol
like TCP/IP in operation, the computer has nothing to connect with—the
machinery by which it connects is simply "not there."
However, the Wi-Fi client adapter will still log stations through
a stumbler utility.
How you disable networking protocols depends on what operating
system you're using. On Windows, you need to bring up your network
connection's Properties window and un-check any networking protocols
that are currently enabled and active. Then reboot.
It's a serious hassle to keep enabling and disabling networking
protocols, so I recommend finding yourself a cheap Windows laptop
that can run at least Windows 98, and making it a dedicated wardriving
machine. I've seen functional if slightly creaky machines like the
IBM Thinkpad 560E available on EBay for as little as $150. Pull
out all the networking stuff, install NetStumbler, and don't use
it for anything else. If keeping your nose legally clean is important
(and it should be!) do not load the machine up with a lot
of network packet sniffing or "password recovery" utilities.
You probably won't run into trouble with law enforcement, but if
you do, you want a machine on your back seat that simply doesn't
have the stuff in it to commit a crime.
Obviously, if everyone enabled encryption (WEP or WPA) on their
APs, autoconnection would not be a problem...but hey, when was Hell
scheduled to freeze over?
|
| What
do I do if I get pulled over while wardriving? |
| |
First of all, cooperate fully with the officer who pulls you
over. Stay calm and don't act like you're smuggling dope or
have an open container under the seat. Let the officer lead the
conversation, and answer his/her questions honestly. Don't assume
the officer knows nothing about wardriving. This might have been
true in 2001, but it's not true anymore.
Even if you're a networking consultant or IT staffer and have multiple
legal uses for packet sniffers and password crackers, I suggest
not having such tools installed on the computer you use for wardriving.
A sidenote: You're more likely to be pulled over if you have a
laptop on the passenger's seat and you're constantly trying to watch
what's going on—and thus weaving all around the road like a
drunk. I suggest leaving your laptop on the back seat. Wardriving
really isn't interactive. Your stumbling utility logs stations automatically
and doesn't require any input from you while it's working. (It will
honk each time it logs a station, which is the only interaction
with it that you really need.) Don't let it be a distraction that
gets you into a crackup.
Also, there are laws in some states that prohibit watching screens
like TVs and computers while you're driving. You can definitely
get a ticket if you're pulled over in those states and are found
to have a working laptop in the front seat somewhere, and the ticket
has nothing to do with wardriving per se. Even if you keep
your laptop in the back seat, try to turn off video if you wardrive
at night, so as not to have the interior of your car awash in a
bluish glow. The police are always watching for weird stuff going
on in their turf. That's their job. Try not to stand out. (I do
all my wardriving during the day.)
|
Part III: Your Wardriving
Rig
|
| Please
give me an overview of a wardriving rig. |
| |
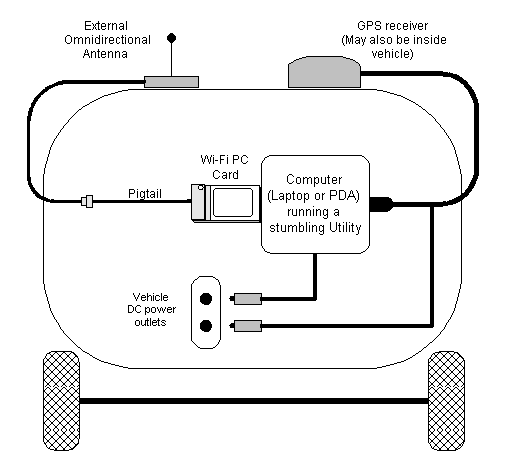
This is a fairly typical setup, and very close to
the one I use. The GPS receiver may be inside the vehicle. Some
GPS receivers connect to the computer via a USB port, and take
their power from the USB port, thus making the "Y" connector
from the GPS receiver unnecessary.
|
| What
sort of antenna works best for wardriving? |
| |
 You
want some sort of omnidirectional vertical antenna, ideally one
that can be mounted on the roof of your vehicle. Again, an external
antenna is optional: You can wardrive with no better antenna than
the one on the end of your Wi-Fi PC card. Such antennas are poor
to begin with, and when they're inside the vehicle the metal structure
of the vehicle shields them from AP signals to some extent. You
will gather a lot more stations using an external antenna.
In my own tests, a roof mounted omni antenna increases the numbers
of stations sensed by at least 50%, and in some cases 100%, over
a PC card's built-in antenna. You
want some sort of omnidirectional vertical antenna, ideally one
that can be mounted on the roof of your vehicle. Again, an external
antenna is optional: You can wardrive with no better antenna than
the one on the end of your Wi-Fi PC card. Such antennas are poor
to begin with, and when they're inside the vehicle the metal structure
of the vehicle shields them from AP signals to some extent. You
will gather a lot more stations using an external antenna.
In my own tests, a roof mounted omni antenna increases the numbers
of stations sensed by at least 50%, and in some cases 100%, over
a PC card's built-in antenna.
The antenna I use is quite popular: FAB
Corp's 5 dBi omnidirectional mag-mount, shown at left. The assembly
rests on a magnetic disk that sticks to the (metallic) roof of your
vehicle, with a length of low-loss coax to take signal to your WI-Fi
adapter inside the car. FAB has the same antenna on an NMO connector,
in case you're willing to drill the roof of your vehicle for an
NMO mount and run low-loss coax down into the vehicle.
I've also had reasonable success wardriving from the back seat
of a taxi by literally hanging a blade antenna from a suction cup
stuck to the taxi's rear window. The cabbies look at me funny sometimes,
but have never objected.
|
| Why
not use a directional antenna? |
| |
You can, and some do, in certain special
circumstances. If you're standing somewhere (on top of a building
or hill) and want to sense stations at a distance, you can use a directional
gain antenna to "warscan" by rotating it on a camera tripod
or just aiming it by hand. |
| Is
a Pringle's potato chip can good for warscanning? |
| |
 In
a word, no. That is, it may work, but it won't work as well as a
"cantenna" made of a metal can like a coffee can or (my
favorite) a spaghetti sauce can. If you're going to go the distance
to make an antenna yourself, make one that works well, not one that
works so-so. Pringle's cans are nonconductive cardboard, and thus
do not operate in waveguide mode, as a metal can does. Rob Flickenger's
shotgun yagi adaptation
of the "classic" Pringle's antenna works, but it's a lot
more work, and in my experiments doesn't do as well as a single
tin can without the yagi elements. In
a word, no. That is, it may work, but it won't work as well as a
"cantenna" made of a metal can like a coffee can or (my
favorite) a spaghetti sauce can. If you're going to go the distance
to make an antenna yourself, make one that works well, not one that
works so-so. Pringle's cans are nonconductive cardboard, and thus
do not operate in waveguide mode, as a metal can does. Rob Flickenger's
shotgun yagi adaptation
of the "classic" Pringle's antenna works, but it's a lot
more work, and in my experiments doesn't do as well as a single
tin can without the yagi elements.
I don't do a lot of warscanning, but I've tried several different
things. At right is a handheld waveguide antenna made from a tin
can that once contained a bottle of spiced rum. (And yes, it's propped
up on an old Tom Swift book!) It works, but it's extremely
directional. A shorter can would make it less directional. I've
had better results in warscanning by mounting a directional antenna
on a camera tripod, and steering with the tripod pan levers. Holding
a highly directional antenna steady long enough for NetStumbler
to get a good fix is a bit of a challenge, especially for distant
stations.
I provide detailed instructions for building cantennas like this
in my
book, including all the math and plenty of photos and technical
diagrams.
|
| What
is a pigtail? |
| |
A pigtail is a short (emphasis: short!) length of microwave-friendly
coaxial cable with connectors on both ends, used to connect a piece
of Wi-Fi gear to an antenna. It's a microwave jumper cable, basically.
It must be short because coaxial cable is very lossy at microwave
frequencies, and the loss is proportional to the length of the cable.
Pigtails typically have an industry standard N female connector
on one end, and one of the several species of Wi-Fi specific connectors
on the other end. You select a pigtail based on the length and on
the type of Wi-Fi connector. (The N connector on one end is usually
a given.) For wardriving you'll probably need one of only two kinds
of pigtails: One for the RMC connector used with the Orinoco PC
cards, or one with the MMCX connector used for several of the lesser
known cards. Such pigtails are typically 19" long and are quite
flexible. Longer pigtails are less flexible, because lower-loss
coax is inherently stiffer.
Ready-made pigtails are available from several firms online, including
FAB Corp. They cost from $20-$30 typically, depending on the length
and the kind of connectors.
|
| That's
a lot of money for 20" of wire! Wouldn't it be cheaper to just
make pigtails myself? |
| |
Yes, a little. However, it's very easy to attach coaxial
connectors to cable badly, especially the very tiny connectors that
are most often used in wardriving. At microwave frequencies (where
Wi-Fi operates) losses in coaxial cable are high, and those losses
skyrocket when a connection is badly trimmed and soldered. Think of
it this way: You might save $5-$8 on the cost of a pigtail by doing
it yourself, but unless you have considerable experience soldering
small connectors to coax, you could end up losing 25% of your station
count (maybe more) on a typical wardrive. Let the professionals do
it. |
| What
GPS receiver works best? |
| |
Pick one; they're all good. Any GPS receiver that can get pick
up enough GPS satellites to get a fix on your position will work
fine. Most people choose a GPS receiver in terms of what other uses
they can make of it beyond wardriving. Many GPS receivers are designed
for independent use (in other words, without connecting to a laptop
or PDA) and have small graphic screens for displaying your current
position. Products like these are a good choice if you're a hiker
or go offroading out in the wilderness. The downside to using such
receivers is that they're typically kept inside the vehicle, and
sometimes that makes it difficult for the receiver to pick up enough
satellites for a fix.
 The
GPS receiver I use is an entirely different concept: It's a little
magnetic puck that sticks to the roof of your car, with a single
USB cable leading in through a window, to plug into your computer.
There's no screen or any other kind of readout on the receiver itself;
it's designed to work with a computer and not independently. The
one I use is called the Holux GM-210, shown at left. The Holux line
is popular in Europe but is little known in the US. I found it at
The GPS Store. It cost
$150 in February 2003. There are others like it. Keep in mind that
a GPS receiver with a magnet in its base must be handled carefully,
and not just tossed it into a bag where it might nestle up next
to your laptop and wipe the hard drive. The
GPS receiver I use is an entirely different concept: It's a little
magnetic puck that sticks to the roof of your car, with a single
USB cable leading in through a window, to plug into your computer.
There's no screen or any other kind of readout on the receiver itself;
it's designed to work with a computer and not independently. The
one I use is called the Holux GM-210, shown at left. The Holux line
is popular in Europe but is little known in the US. I found it at
The GPS Store. It cost
$150 in February 2003. There are others like it. Keep in mind that
a GPS receiver with a magnet in its base must be handled carefully,
and not just tossed it into a bag where it might nestle up next
to your laptop and wipe the hard drive.
Note well that NetStumbler does not directly accept GPS
coordinate data from USB ports. The Holux is a USB device, but it
comes with an installable "port bridge" driver that grabs
one of the PC COM ports (I use COM5) and places data arriving from
the receiver on the USB port onto the COM port, where NetStumbler
can find it. This works very well, and because power is provided
to the receiver over the same USB cable as the serial data itself,
this makes a separate power cable and connector unnecessary. I also
use the Holux to display a "you are here" marker while
we're traveling by car, in conjunction with Microsoft MapPoint,
so its use is not limited to wardriving. (My wife does the navigating
and reads the laptop screen, by the way. Watching a laptop while
you're driving is dangerous, and illegal in some areas!)
|
Part IV: NetStumbler
|
| What
is NetStumbler? |
| |
NetStumbler (more formally, Network Stumbler
for Windows) is a stumbling utility for 32-bit Windows. It is a free
and relatively simple installable program that listens for Wi-Fi access
point beacons and logs them to a disk file, with all the information
that the AP makes publicly available. |
| Where
do I find it? |
| |
NetStumbler is free and may be downloaded from the NetStumbler.com
downloads page. Unlike much free software, new releases are posted
infrequently; you needn't check every day or even every month for
a new release. And although NetStumbler is free, the author, Marius
Milner, welcomes donations, which may be sent to him via PayPal. See
Marius' blog for details on
how to donate. |
| Is
NetStumbler a wireless network cracking utility? |
| |
Emphatically not. Netstumbler is a good and courteous listener.
It only records those elements of data that the access point (AP)
makes public. It has no machinery for sniffing packets, reverse-engineering
passwords, or even connecting to an unprotected network. Furthermore,
NetStumbler respects the wishes of network owners in terms of the
public visibility of their networks: If the owner of an AP disables
the AP's beacon broadcast, NetStumbler will not detect it.
|
| What
is NetStumbler typically used for? |
| |
NetStumbler has three major uses:
- Wardriving, as described earlier in this FAQ.
- Detecting rogue access points in large networks used by many
people. A rogue access point is simply an access point
that has been connected to a network without the permission or
knowledge of the network administrator. These are a hazard in
a number of ways, but primarily in that they are connected behind
the company firewall and thus short-circuit most of the network's
security technology. (As someone said on the NetStumbler forums,
it's like hanging a category 5 network cable out the window down
to the parking lot.) To find rogue access points, an administrator
simply walks around the area where the network reaches with NetStumbler
running on a laptop or MiniStumber on a PDA. If any access points
are in the vicinity of the network, NetStumbler will report them,
and the network administrator can remove them if they're not an
official part of the network.
- Directly sensing the coverage of an AP's radio field. NetStumbler
includes a high-resolution field strength and signal-to-noise
ratio display. By walking around with a laptop running NetStumbler,
you can find weak spots and dead spots in an AP's coverage, as
well as determine with fair accuracy the outer limits of an AP's
useful range. NetStumbler is also useful in testing the relative
effectiveness of Wi-Fi antennas, by placing a laptop running NetStumbler
in a fixed position, and then aiming antennas at it from some
distance away. If the antennas are all at the same distance from
the laptop, NetStumbler's readings will accurately reflect how
well the antennas work with respect to one another.
|
| What
client adapters does NetStumbler work with? |
| |
NetStumbler author Marius Milner actively enhances the product,
adding more supported client adapters on a regular basis. He posts
a list of supported client adapters in the readme file for the NetStumbler
software. This readme file is included in the NetStumbler download
archive, but it's also posted
on the Web. This is the first place you should look to check
for specific client adapter support.
On the other hand, there are similarities in drivers and in client
adapter hardware, and often an adapter that is not on the official
"supported" list will be similar enough to a supported
adapter to work. This whole business is made worse by the fact that
some adapters will work using Windows XP drivers and won't work
using drivers for other operating systems. If you have an adapter
that isn't on Marius' supported list, try it! This is especially
true if you're using Windows XP. Your chances improve if you have
the latest firmware loaded on the adapter, and also the latest OS
drivers from the manufacturer.
Much discussion of this issue happens on the NetStumbler
Forums. I advise using the Search function to look for the names
of specific cards that you're interested in. Use Search. Don't just
post a question that may have been asked and answered fifty times
already.
|
| What
is the best client adapter to use with NetStumbler? |
| |
There is no one answer to this question. The way to approach it
is to look at the four variables that govern a client's suitability
for use with NetStumbler. I list them in their order of importance:
- Technology. 802.11b and 802.11g are the only wireless
technologies supported by NetStumbler. 802.11a does not (currently)
work at all. TI's 802.11b+ chipset has been reported by some to
work, but my experiments with D-Link's DWL-650+ PC card have not
borne this out.
- NetStumbler compatibility. As I mentioned above, not
all 802.11b Wi-Fi clients work with NetStumbler. You'll have to
check Marius Milner's list of supported cards regularly, and monitor
pertinent traffic on the NetStumbler
Forums. The operating system you're running also makes a difference.
I have found that Wi-Fi client cards that don't work under Windows
2000 will work under WIndows NT. It's hard to know for sure, however,
until you try.
- Antenna jack. Although not strictly required, it's very
difficult to get effective results with a laptop using a PC card's
tiny integrated "bulge" antenna. A fairly small cohort
of PC cards has a tiny coaxial jack into which you can plug a
coaxial connector leading (via a short run of coaxial cable) to
a vertical antenna on top of your vehicle. My experiments have
shown that using a PC card's integrated antenna alone will gather
only 50%-60% as many stations as a vertical antenna outside the
vehicle.
- PC card receiver sensitivity. Some (but by no means all)
manufacturers of Wi-Fi PC cards publish a receiver sensitivity
figure in dBm. This figure specifies the amount of radio power
that must be delivered by the card's antenna to the receiver circuitry
for a station to be effectively received above the noise. The
number is usually from -80 dBm to -90 dBm. The larger the number,
the more sensitive the card, because the values are negative.
-90 dBm is less power than -80 dBm, so if a receiver can pick
up a signal at -90 dBm, that's better. (Such receivers are rare.
Most fall in the -80 dBm range.) Caution: Sensitivity is something
to consider, but only if the card is known to be compatible
with NetStumbler. In practice, differences of a few dBm will not
be significant in terms of numbers of stations logged.
The bottom line is that you need a card that works with NetStumbler
and also has a jack for an external antenna. The most commonly used
cards that meet both of these criteria are the Orinoco Silver and
Orinoco Gold. Most people use the Gold card; the Silver card is
identical except that it only supports 64-bit WEP, which doesn't
matter for wardriving. If you don't already have a PC card adapter,
get the Orinoco Gold card; it's cheap, reliable, and completely
supported by NetStumbler. Another reason to use the Orinoco PC cards
that is not widely known is that their firmware discriminates against
something called "weak IV" values. Weak IV values are
one way that crackers break into wireless networks. I explain this
in detail in my
book; it's off-topic for a wardriving FAQ, but weak IV discrimination
is a very good feature to have in a Wi-Fi client adapter
and access point.
|
| Do
CardBus PC cards work with NetStumbler? |
| |
Whether a client adapter is a 16-bit PCMCIA card or
a 32-bit CardBus card doesn't matter to NetStumbler. However, it may
matter to your laptop. CardBus is a fairly recent technology, and
laptops built before 1999 generally don't have CardBus slots. If you
buy a CardBus card and your laptop lacks a CardBus slot, the card
won't fully insert and will not function at all. |
| How
do you use GPS with NetStumbler? |
| |
NetStumbler accepts GPS data through any of the PC's serial ports.
Note that "serial" does not mean "USB" here;
NetStumbler only accepts serial data on COM ports. (There is a dodge
around this that I've used; see below.) In terms of GPS data formats,
the older versions of NetStumbler only accepted NMEA (National Marine
Electronics Association) 183 data. The latest version will also
accept Garmin Binary, Garmin Text, and Tripmate formats. Any GPS
receiver that can emit one of those formats should work with NetStumbler.
You select the COM port and the GPS data format from the GPS tab
of the Options dialog. You bring up that dialog by selecting View|Options
from NetStumbler's main menu.
GPS receivers that communicate primarily through a USB port often
come with "port bridge" software, which is an installable
utility that "maps" a USB port onto a COM port. The receiver
still reports its data through the USB port (and draws its power
from the USB port, which I consider a big plus—fewer cables!)
but the bridge utility also sends the data to the COM port driver.
Software like NetStumbler that listens for data on a COM port can
thus acquire data from a USB receiver. Marius has indicated that
he intends to expand direct USB support of GPS over time, so you
need to watch for updated releases of NetStumbler.
|
Part V: The Practice
of Wardriving
|
| What
wardriving approach gathers the most stations? |
| |
Easy: Go slow and stay off the superhighways. Consensus is that
a speed of about 35 MPH is ideal for wardriving. Stumbler programs
need some time to work, and if you roar past at 80, the more distant
stations will not be within range long enough for the stumbler
software to log them. My experiments also show that if you spend
most of your wardriving time on limited access highways, you'll
miss stations compared to driving on surface streets. On a superhighway
you typically go faster (unless you're in LA, I guess) than surface
streets, and you're also farther away from buildings where the
APs are and will thus miss more of them.
Note well that Kismet is much slower to scan the full 802.11b channel
space than NetStumbler, so if you're wardriving with Kismet it's
even more important not to scream down the street at 75 MPH. Kismet,
being fully passive, has to take time to listen for APs;
NetStumbler, on the other hand, emits 802.11b probes frequently
to speed of the process of AP discovery.
|
| How
can I make sure I've logged every station in my area? |
| |
It's all about planning and
record-keeping. Do what I do: Get a street map of the area, and block
it out into sectors with a highlighter. Then, starting with one of
the sectors, go up and down every last street shown on the map within
that sector, and highlight the street as you stumble it. Repeat for
each of the sectors. This approach guarantees that you won't miss
anything within a given sector, and has an additional benefit: Logging
a station from several different directions (as you stumble nearby
side streets) allows mapping systems like WiGLE and WiFiMaps to triangulate
an AP's precise position and/or coverage area. (More on WiGLE and
WiFiMaps later in this FAQ.) This, of course, assumes you have GPS
data coming in while you wardrive. |
| What
is a "standard wardrive?" |
| |
This is my term for defining
a route and then wardriving it on a regular basis (say, weekly or
monthly) and keeping the logs for each drive so you can track the
changes in the Wi-Fi network installed base over time. The easiest
way to do this is use your daily commute, if it takes you past enough
stations to be useful. If not, then simply pull out a map and choose
a route that will net you at least fifty stations, the more the better
for statistical usefulness. Each time you stumble your standard route,
save the log file with a name that includes the date and the name
of the route taken. (I have three standard wardrives.) By all means
merge your logs into a master logfile containing all your stumbled
stations from all routes and runs, but keep separate copies as well
for analysis. |
| |
Part VI: Mapping Sites
and Software
|
| How
can I plot the stations that I log on a map? |
| |
There are several different ways to plot stumbled stations on a
map. The systems I have used myself are WiGLE, WiFiMaps and Stumbverter.
For any of these systems, you must have used a GPS receiver to add
geographical coordinate data to your stumbling log files. The coordinates
provided by GPS are what locate the stations on a map. The caution,
of course, is that your GPS receiver reports your position
as you received a station's beacon, not the position of the
station itself! (This should be obvious but it's easy to forget.)
Multiple readings on the same station allow some utilities to triangulate
an approximation of the station's position and range, but how accurate
such approximations are is a little unclear. WiGLE seems to do the
best job on that score, but even then, if you only sense stations
from one direction, the triangulated position will be skewed in
one direction.
|
| How
does WiGLE work? |
| |
WiGLE (Wireless Geographic Logging
Engine) is a complete system for mapping stumbled APs, and includes
a Web database and several mapping clients. As best I know, it's
the oldest such system in existence, and has been in operation since
September 2001. Here's how it works, from a height: Users upload
log files containing records of stumbled APs, which are processed
and added to a database. "Map pack" data files may be
downloaded by county (US only) and plotted on-screen using one of
the WiGLE clients.
Like WiFiMaps (see below) WiGLE performs triangulation calculations
on multiple readings of each stumbled station, in order to more
precisely determine the actual physical location of the station.
(Remember that the GPS coordinates recorded for a station during
a wardriving run are your location when your Wi-Fi client
adapter hears the station, not the coordinates of the station
itself!) Each station is plotted as a point on a map, and you can
pan and zoom to get the full picture of any given county.
The WiGLE system includes several different clients:
- JiGLE is the oldest, and is written in Java. It should run anywhere
Java will run.
- DiGGLER is a native-code Windows client written in Delphi. It
does basically what JiGLE does, but does not require the Java
VM. It's small, fast, and doesn't mess with your registry. (Can
you tell I'm a Delphi fan?) It is, however, limited to running
under 32-bit Windows.
- PRInGLE is a client for Palm OS, which is not yet released but
should be soon.
The clients come with sample maps, but in actual use, you must
request a WiGLE map pack for download. These are free, and are available
for any county in the US. (You must register with the WiGLE system
to download map packs.) On the backend, WiGLE map packs are generated
by RiGLE, the using public domain TIGER geographic databases distributed
by the Federal Government. The generated maps are thus not encumbered
by anyone else's copyrights.
Wardrivers may upload log files in any of several formats, including
NetStumbler and MiniStumbler (export as text); DStumbler text, and
the Kismet CWGD, CSV, XML, and GPS formats. Uploads are handled
through a page on the WiGLE Web site. Uploaded stations are immediately
available for downloading in a map pack. You can upload the results
of a wardriving run, and then immediately download an updated map
pack reflecting the results of that run. There are currently over
260,000 stations present in the WiGLE database. (April 2003.)
|
| How
does WiFiMaps work? |
| |
WiFiMaps.com is a Web site
operated by zhrodague.net, which allows wardrivers to upload NetStumbler's
exported text-format log files, and then plots those uploaded logs
on street maps. You can then look up the maps for a given city or
town and then pan around to see where all the access points are
located. For access points that have multiple readings in the database,
the software triangulates a coverage region, which is shown as a
shaded circle of a suitable diameter. (If an AP has only one reading,
or for some reason not enough readings to allow the triangulation
to work, it's indicated as a small triangle and its SSID.)
All wardrivers are invited to upload their exported text-format
log files from NetStumbler and Kismet to the WiFiMaps.com database.
Supported upload formats are NetStumbler's text export (full) and
Kismet CSV.
|
| How
does StumbVerter work? |
| |
StumbVerter is a free utility from Sonar
Security that converts NetStumbler export logs into Microsoft
MapPoint maps. StumbVerter uses the MapPoint server and puts a MapPoint
map in a window, showing any imported stations as small icons.
The downside to StumbVerter is that it requires the use of MapPoint,
which is fairly expensive as commercial software goes. (StumbVerter
itself is free.) On the other hand, MapPoint is extremely useful
for travelers, and generates nicely rendered maps for the entire
US. (Maps are available for some areas overseas, but I've not tried
those.)
|
|
Part VII: Sources, Odds
and Ends
|
| Please
list some sources for wardriving software and hardware. |
| |
Software:
- NetStumbler.com, for
the NetStumbler and MiniStumbler utilities.
- Aerosol,
a simple wardriving utility for Windows that supports some USB
client adapters, including Linksys WUSB11. Good device support,
fairly minimal feature set. Requires a protocol driver like WinPCap.
- Kismet is probably
the most commonly used wardriving utility for Linux. It works
in monitor mode and can detect APs whether or not their broadcast
beacons are operating.
- AirTraf,
a curses-based (i.e., text mode) wardriving utility for Linux.
A CD-bootable version for Windows users is promised; this will
boot into Linux without affecting the underlying system. Not available
yet.
- DStumbler
is part of BSD-Airtools, and is a curses-based wardriving utility
for BSD Unix.
- MacStumbler is similarly
the leading utility for the Mac. OS/X only, and so far requires
AirPort wireless hardware.
- KisMac is a wardriving utility
for Mac OS/X that works in monitor mode (like Kismet, its only
relationship thereto) and can detect APs that have their beacons
disabled.
- PocketWarrior
for PocketPC supports Prism-based clients cards on the PocketPC
platform. Theoretically works with any NDIS 5.1-compatible Prism
driver, but it's always best to check the list of supported cards.
- WarLinux,
a CD-bootable version of Linux created specifically for wireless
auditing. I haven't used it yet but it's a promising idea: Configure
Linux with all the machinery already in place for wireless network
auditing.
- Warglue
is a suite of console (text-mode) utilities for converting among
the three major wardriving logfile formats: NS1, (NetStumbler)
Kismet, and Wiscan. Warglue also contains a utility for knocking
out defective GPS coordinates from a logfile.
Several other pertinent utilities exist (see the list
at wardriving.com) but
the ones listed above are the main ones.
Links:
- Wardrive.net is by considerable
margin the biggest and best collection of wardriving and Wi-Fi
security links out there. The page includes pertinent Usenet newsgroups,
mailing lists, and print books. Highly recommended.
Hardware:
- My personal favorite source for wardriving hardware (antennas
and connectors, primarily) is Fleeman,
Anderson, and Bird. (FAB, to insiders.) They sell goods related
to Wi-Fi generally, but have paid special attention to the sorts
of things wardrivers use. Their omnidirectional mag-mount antenna
beats anything I myself have ever tried, including Pringle's and
various tin-can antennas. They also sell every conceivable type
of pigtail, silver-plated coaxial connectors, and microwave-capable
coaxial cable.
- Hyperlink Technologies
is another major dealer in Wi-Fi hardware that I've heard good
things about, though I've not used them personally. Great prices,
broad selection, including the best deal I've seen on a 24 dBi
grid parabolic. (They don't lean as much toward wardriving gear
as FAB.
|
| What
other wardriving stuff is available? |
| |
- CafePress has a
large selection of wardriving stuff, including mugs, caps,
T-shirts, teddy bears, barbecue aprons and—egad—women's
thong panties.
- HackerStickers.com
has "Wardriver" and "MacStumbler" bumper stickers
and a Church of Wi-Fi "fish" sticker.
- "Wardriver"
stickers for the back window of your vehicle—or the back
of your laptop. Vinyl.
|
|
|
|